Can the seemingly intangible world of the Internet of Things (IoT) truly be mastered, or is it destined to remain a complex enigma? The relentless march of technology, fueled by interconnected devices, is fundamentally reshaping our daily experiences, demanding a deeper understanding of how we command these digital extensions of ourselves.
The quest to control devices over the internet has evolved from a niche technical challenge to a mainstream necessity. Modern life has become intricately woven with smart technologies, from the simplest smart home appliances to the most complex industrial systems. We are increasingly reliant on the ability to issue commands and receive feedback remotely, ensuring seamless operation and efficient management of these systems. This capability underpins the very fabric of IoT, making it indispensable for applications ranging from environmental monitoring to personalized healthcare. The absence of a straightforward method of remotely controlling these devices can frustrate the user experience and limit the potential of these devices. This has given rise to several methodologies, each with its unique challenges, to overcome the obstacles that come with remote device control. The ideal method is the one that seamlessly combines security, accessibility, and simplicity, ultimately empowering users to harness the full potential of the IoT ecosystem. The success of remote command execution relies heavily on a few important factors: the device's continuous connection to the network, its capacity to interpret incoming commands, and its ability to convey its operational status.
| Aspect | Details |
|---|---|
| Continuous Connectivity | The device must maintain a stable connection to the internet or a network that facilitates communication. This is typically achieved through Wi-Fi, cellular data, or other network technologies. |
| Subscription to a Topic | The device should be subscribed to a specific topic or channel where incoming commands are published. This topic acts as a communication bridge. |
| Command Reception and Processing | The device should be able to receive the command, which is a set of instructions sent over the internet, and execute it. |
| Feedback Mechanism | The device should have a way to acknowledge and report on the results of the command execution. |
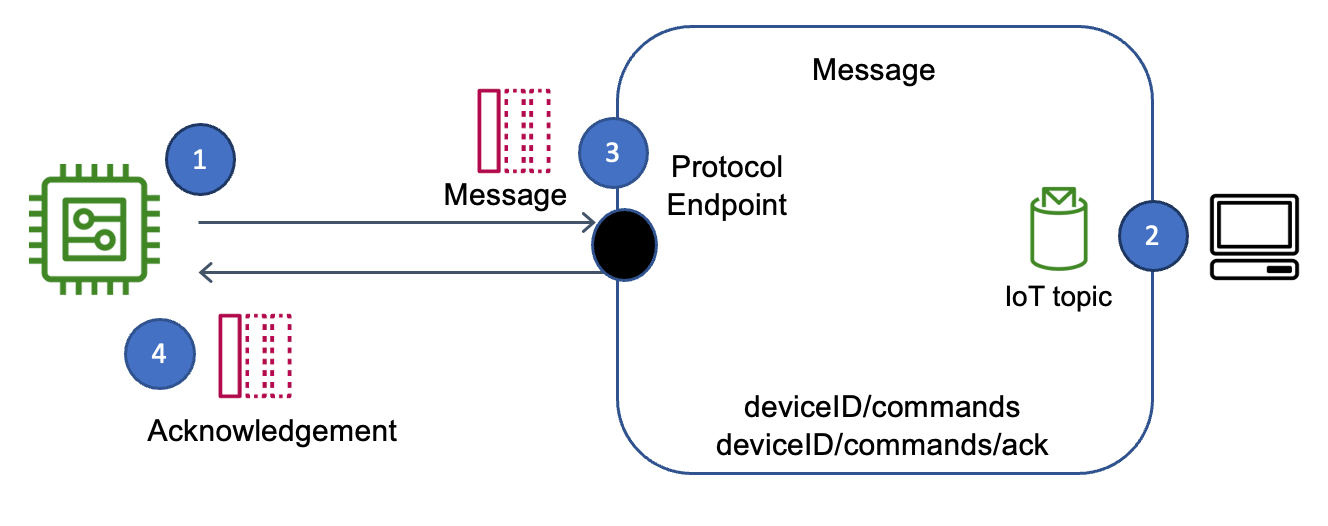
At the heart of this technological revolution is the concept of remote command executionthe ability to control devices from a distance. This seemingly straightforward function has proven to be a complex undertaking, requiring careful consideration of several critical elements. The seamless operation of this mechanism hinges on a few fundamental principles: consistent network connectivity, the ability of devices to correctly interpret incoming commands, and effective channels for reporting command execution status. This framework empowers users to issue instructions, monitor performance, and receive real-time feedback, all without physical proximity to the device. The potential of remote command execution extends far beyond mere convenience; it drives efficiency, enhances safety, and opens doors to novel applications across various industries.
- Brigitte Macron Age Birthdate Facts You Didnt Know
- Tiktok Coins Buy Recharge Send Gifts Ultimate Guide
Consider the implications in industries like agriculture, where remote monitoring of environmental conditions and automated irrigation systems can maximize crop yields and minimize water waste. Healthcare is another arena where remote control is essential. Remote patient monitoring devices, for instance, allow healthcare professionals to track patients' health metrics in real-time and provide immediate interventions. This is a notable step towards a more proactive and personalized healthcare paradigm. Within the realm of industrial automation, the capability to remotely control machinery and equipment is crucial. This optimizes operational efficiency and enables maintenance tasks to be carried out more efficiently. This allows for quicker troubleshooting and reduces downtime, contributing to enhanced productivity.
However, the path to achieving these benefits is not without its obstacles. Security is paramount in a world where compromised IoT devices can be exploited to infiltrate larger systems or cause physical damage. The design of a remote command execution system must prioritize security, including robust authentication protocols, encrypted communication channels, and frequent vulnerability assessments. Ensuring reliable and secure connectivity is critical in areas where a constant internet connection cannot be assured. This might involve the adoption of redundant communication methods, such as satellite connections or local area networks. The diversity of IoT devices also poses a challenge. Different devices have various protocols, communication methods, and processing capabilities. Any viable approach must be adaptable to diverse device environments, supporting an extensive range of hardware and software platforms. The complexity is further amplified by the need for scalable architectures that can handle a growing number of devices and increasing data volumes.
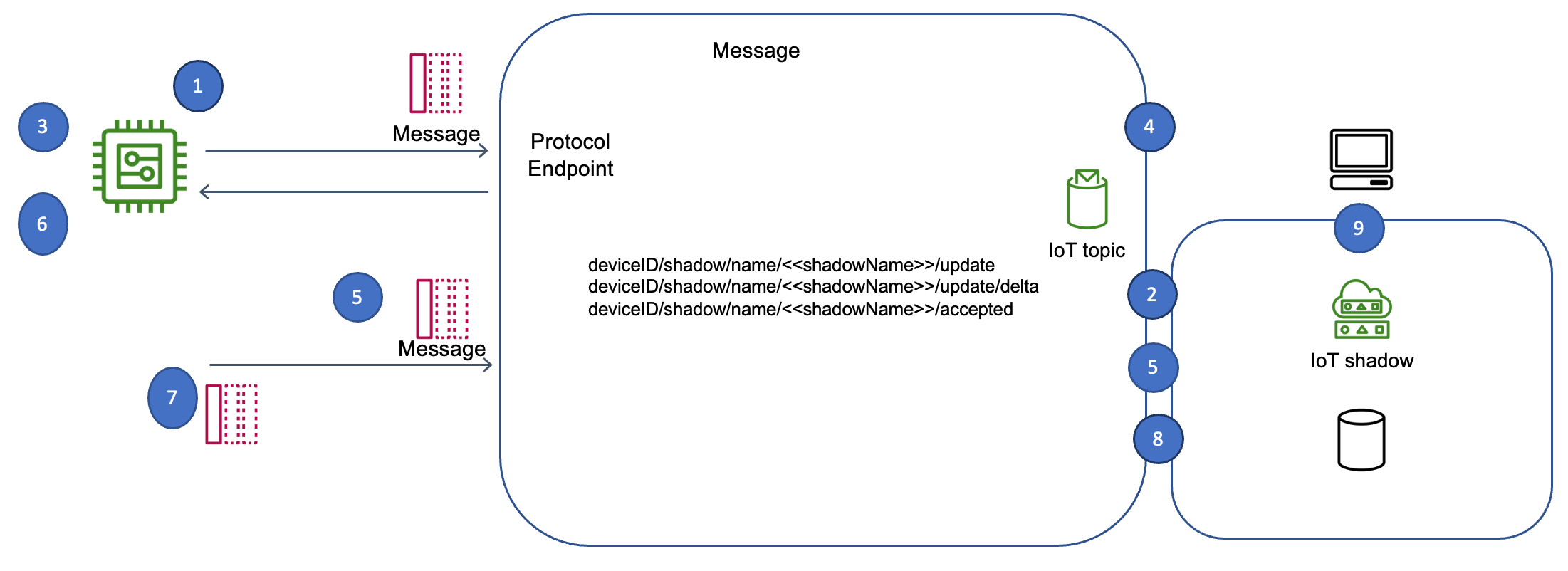
One common approach involves utilizing a message broker, such as MQTT (Message Queuing Telemetry Transport), to facilitate the exchange of commands between a central control application and the IoT devices. In this scenario, devices subscribe to a particular topic on the broker and listen for incoming commands. When a command is sent, it is published to the designated topic, and all subscribed devices receive it. The devices then execute the command and, if necessary, send a confirmation back to the controller. This method provides a flexible and scalable solution and enables asynchronous communication, which is crucial for scenarios with unreliable connectivity. However, this setup requires careful consideration of security measures, such as the use of encryption and access control lists. It can also be complex to manage different devices and ensure the compatibility of command formats.
- Explore Salat Insights Meanings About Allahouma Google Discover
- Exploring Movierulz Latest News Updates Plus Challenges
Another approach involves the use of cloud-based IoT platforms, such as AWS IoT, Azure IoT Hub, or Google Cloud IoT. These platforms offer a comprehensive suite of services for device management, data storage, and analytics. The platform acts as a centralized hub for managing commands, device configurations, and security. It can also be used to monitor device health and performance. Using cloud platforms, commands can be sent to devices over the internet. The platforms offer features such as device shadow, where the device's current state is maintained and reflected in the cloud, making it easier to manage devices and track their activity. These platforms often provide a range of tools to streamline development and deployment, offering a more managed approach to IoT applications. However, using these platforms can lead to vendor lock-in and require a high level of expertise to set up and maintain.
Furthermore, edge computing is growing in importance. It entails moving data processing and analysis closer to the data source, which reduces latency, bandwidth consumption, and reliance on cloud connectivity. Edge devices, such as gateways or specialized computing units, can execute commands locally, filter data, and pre-process it before sending it to the cloud. This is important for real-time applications and scenarios where network connectivity is limited. For example, a downstream device might use Bluetooth to connect to the IoT edge device, which then connects over the internet to IoT central. This approach can help reduce the costs of sending data to IoT central. Enabling devices that cannot connect directly to IoT central to connect through the IoT edge device is one example of how edge computing can be used to expand the IoT network. Edge computing, in conjunction with cloud-based IoT platforms, offers a hybrid approach that enables businesses to balance the benefits of local processing with the scalability and comprehensive services provided by the cloud. However, this also increases the complexity and requires careful planning and management of edge devices.
Voice control is another rapidly evolving interface for IoT devices. Systems like Alexa from Amazon and Google Assistant have gained popularity, enabling users to control devices using speech. This allows users to use voice commands to control their gadgets. This development underscores the need for intuitive and user-friendly interfaces. Voice command is a standout method for managing smart devices. This method requires integration with voice assistants, language processing, and understanding of context. This approach provides a natural and simple user experience, but it can also present issues with accuracy, privacy, and security. Voice commands require a strong network connection and are subject to noise interference. To ensure the security of voice commands, encryption and authentication are required. Voice control can improve user experience and simplify device control, despite its limitations.
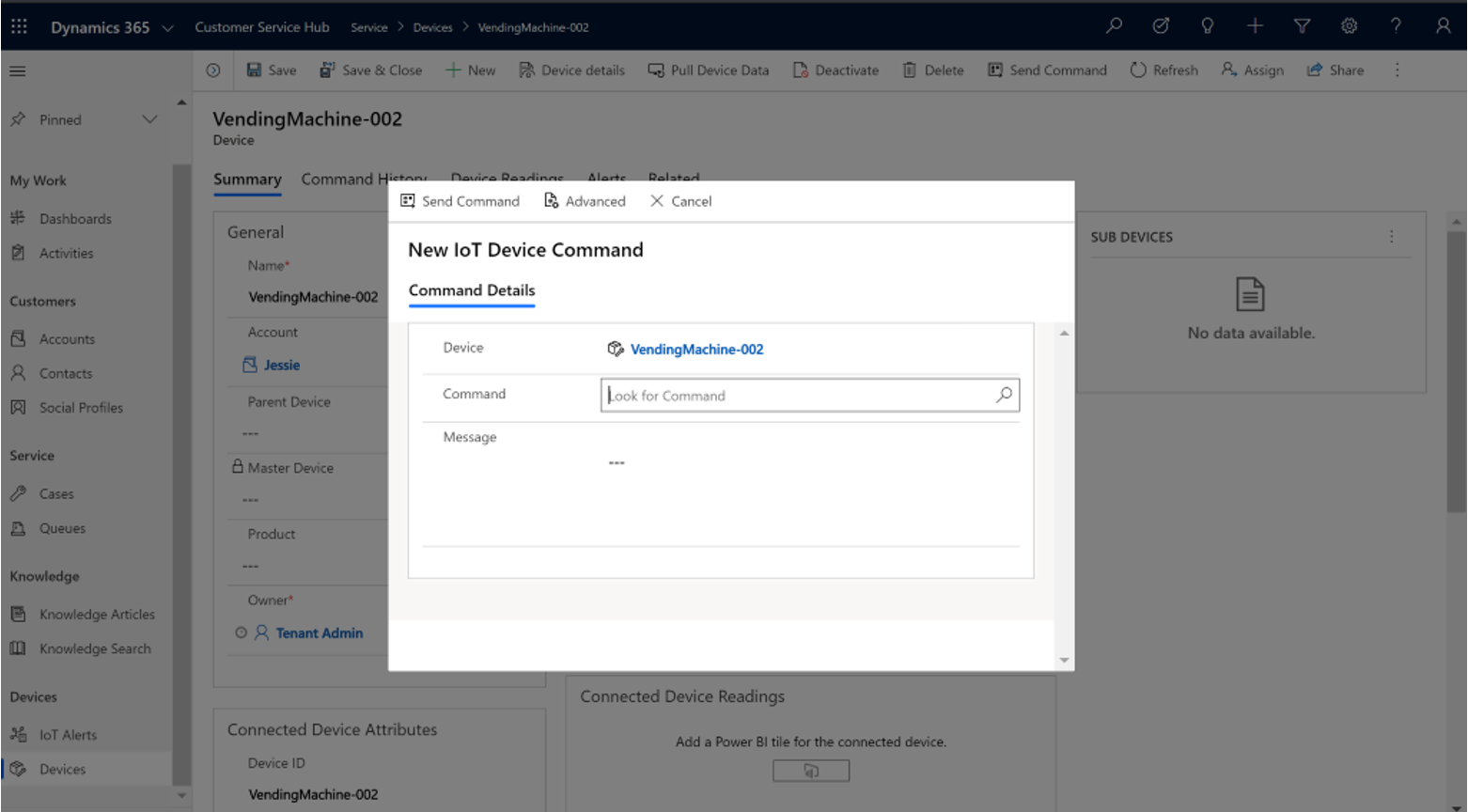
The process of implementing remote command execution is often iterative, with an initial focus on testing connectivity and confirming that a device can receive and execute simple commands. This phase is critical to identify and resolve any initial configuration or network issues. One can use this approach to send test data from the device to test AWS IoT rule actions. When you start a command execution from the AWS IoT console, or use the startcommandexecution API to send the command to your device using the commands request topic. If the request is successful, the command execution status changes to created. This step ensures that the device can communicate with the control system and is able to send test data from the device to test AWS IoT rule actions. Subsequent stages involve the design of more complex commands and the integration of response mechanisms, such as notifications and status updates. The key is to validate and refine the approach to ensure reliability and security at all stages. This includes rigorous testing to detect bugs and security flaws. An essential part of the development process is the ongoing monitoring of performance and the provision of tools for debugging and troubleshooting.
Securing remote command execution necessitates a multi-layered approach. Strong authentication mechanisms, such as multi-factor authentication and digital certificates, are crucial to verify the identity of both the control application and the IoT device. This helps prevent unauthorized access. The communication channels must be encrypted using protocols like TLS (Transport Layer Security) to safeguard data in transit. This prevents eavesdropping and data tampering. Implementing access control policies and role-based access control (RBAC) further restricts command execution to only authorized users or applications. Regular security audits and vulnerability assessments are important to identify and address any potential weaknesses in the system. The implementation of these practices will ensure a secure and trustworthy remote command execution environment. This promotes the safe operation of linked devices and the protection of sensitive data.
The future of IoT and remote command execution is poised for rapid expansion, driven by technological advances and the rising demand for intelligent, connected devices. The integration of Artificial Intelligence (AI) and Machine Learning (ML) is crucial. AI-powered systems can analyze device data and predict future needs, enabling automated control and proactive maintenance. Blockchain technology offers secure and transparent command execution, making the system more resistant to hacking attempts. The evolution of 5G and 6G networks promises faster, more reliable, and lower-latency communication, paving the way for real-time control of devices. These technologies support more complex IoT applications, such as autonomous vehicles and augmented reality. The Internet of Things (IoT) has paved the way for new methods to manage smart devices, and voice command has become a standout. In the future, these advancements will transform the way we interact with and control the ever-growing array of connected devices, enhancing their capability and ensuring that IoT remains an essential part of our lives.
- Bellakaths Music New Releases More On Spotify Apple Music
- 2025 Movies Streaming Explore New Releases