Are you struggling to secure your Raspberry Pi and safeguard it from potential threats? Understanding and implementing a robust firewall is not just a recommendation; it's a fundamental necessity for protecting your digital assets and ensuring the privacy of your data.
In today's interconnected world, where cyber threats are constantly evolving, the need for robust security measures is paramount. The Raspberry Pi, a versatile and affordable single-board computer, has gained immense popularity among hobbyists, educators, and professionals alike. Its adaptability and compact size make it an ideal platform for a wide range of projects, from home automation to server applications. However, its open nature also makes it a potential target for malicious actors. A Raspberry Pi connected to a network, without proper security measures in place, can become a gateway for unauthorized access, data breaches, and other cyberattacks. Therefore, implementing a firewall is a crucial step in protecting your Raspberry Pi and the sensitive information it may hold.
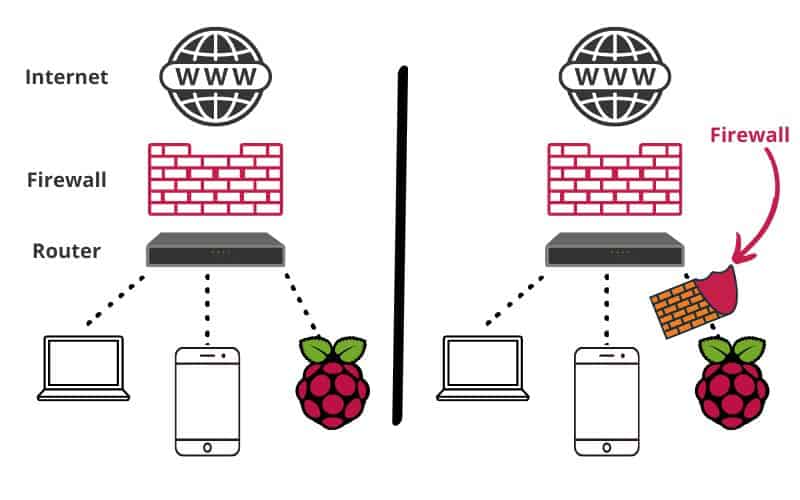
The initial query, "How do I access my Raspberry Pi firewall?" reflects a common concern among users, highlighting the need for accessible and user-friendly methods to manage and configure their security settings. The importance of this question is evident, as it directly addresses the core issue of securing a device that often serves as a central hub for various digital activities.
- Daisy Melanin Viral Video Whats Trending Details Here
- Search Fails Ugly Explained What You Need To Know
Many users encounter difficulties when first attempting to secure their Raspberry Pi. They might struggle with the technical jargon or the complexities of setting up a firewall. The good news is that there are multiple options available, some easier to implement than others, but all aiming to achieve the same goal: protecting your device and your data.
One of the most effective and user-friendly options for securing your Raspberry Pi is the Uncomplicated Firewall (UFW). UFW provides a simplified interface for managing your firewall rules, making it accessible even for those who are new to Linux and networking concepts. UFW is designed to be easy to configure and use, even for users with limited technical expertise. This simplicity, however, does not compromise its effectiveness. UFW can effectively block unauthorized access to your Raspberry Pi, preventing malicious actors from exploiting vulnerabilities and gaining access to your data. The command to install UFW on your system is simple: sudo apt install ufw. The software is readily available through the Debian package repositories.
The second option is iptables. Iptables is a powerful and highly customizable firewall solution that offers a great level of control over your network traffic. It is the more mature, traditional, and flexible approach to firewall management. However, iptables also has a more complex syntax and requires a deeper understanding of networking concepts. For users who are comfortable with command-line interfaces and advanced configurations, iptables can provide the ultimate in control and customization. But for users who are just starting out and simply want a user friendly solution, using UFW is recommended.
When implementing a firewall, the initial step is often to identify the necessary firewall rules. These rules define what types of network traffic are allowed to pass through your Raspberry Pi's network interfaces and which are blocked. This involves determining which services need to be accessible from the outside world and which should be restricted. For example, if you are running a web server on your Raspberry Pi, you will need to allow incoming traffic on port 80 (HTTP) and port 443 (HTTPS). If you need to remotely access your Raspberry Pi via SSH, you will need to allow incoming traffic on port 22. The remaining ports and network traffic, especially those associated with less-secure protocols, should be blocked to minimize the risk of security breaches.
Once the rules have been configured, you can activate the firewall. With UFW, the command is straightforward: sudo ufw enable. This command activates the firewall and starts applying the rules you have defined. It's essential to verify that the firewall is working as expected by checking its status. Using the command sudo ufw status will display the status of the firewall, including the active rules. This helps ensure that the firewall is running correctly and effectively protecting your Raspberry Pi.
There are several ways to manage the firewall. If you use UFW, there are many options, such as adding rules to allow or deny specific ports, configure IP addresses, or enable or disable certain services. The primary commands include sudo ufw allow to allow traffic on a particular port, sudo ufw deny to deny traffic on a particular port, and sudo ufw delete allow to remove an existing rule. You can also allow and deny specific IP addresses, subnets, and network interfaces. Using the right rules will help to create a balanced system.
Another important consideration is the automatic startup of the firewall. In order to ensure that your Raspberry Pi is protected from the moment it boots up, it's crucial to configure the firewall to start automatically. With UFW, this can be done easily by enabling it. To configure the automatic startup, type the command sudo ufw enable. It will automatically enable the firewall when the Raspberry Pi starts, providing continuous protection.
A good firewall is only one layer of security; it's important to consider other measures to increase the security of your Raspberry Pi. Securing the SSH service by changing the default port (22), implementing strong passwords, and disabling password-based authentication in favor of SSH keys is a good start. Regularly update the operating system and software packages, and also keep your system updated. Enable automatic security updates and you can stay protected against new threats.
If you find yourself unable to log in to your program from a web browser despite having SSH enabled, it is usually caused by a blocked port. Ensure that port 80 (for HTTP) or port 443 (for HTTPS) is open in your firewall rules. To do this with UFW, use the commands sudo ufw allow 80 and sudo ufw allow 443. The most likely cause of your issue is a blocked port in your firewall, so you should try these steps. Another common issue is incorrect network configuration. Make sure your Raspberry Pi is configured to use the correct IP address, subnet mask, and gateway settings. If you still have problems accessing your program, try installing a desktop environment such as Raspberry Pi Desktop, and checking if the program runs, which can help isolate whether the issues are related to the server software, or the network configuration.
Securing your Raspberry Pi with a firewall is not a one-time task, but an ongoing process. It should be regularly reviewed and updated to adapt to new threats and changing requirements. This includes regularly reviewing the firewall logs for suspicious activity, monitoring network traffic, and keeping the firewall rules up to date. To help you with this, many operating systems and distributions now offer tools that can assist with this, and can even automatically scan for malware.
One option for protecting your Raspberry Pi with a software firewall is Debian's UFW service, which is much more simple to use and configure. Using the easy-to-use UFW is always a good choice for beginners, as it allows you to easily set up rules.
The importance of securing Raspberry Pis cannot be overstated in today's digital landscape. While the Raspberry Pi is versatile and valuable, it is also vulnerable to attacks if not properly secured. Implementing a firewall is one of the most important steps to securing a Raspberry Pi.
To recap, setting up a firewall on your Raspberry Pi is an essential task that protects your device from cyber threats and enhances the security of your network. By understanding the different firewall options available and implementing the appropriate rules, you can take a significant step towards safeguarding your digital assets and enjoying the full potential of your Raspberry Pi.
Your Raspberry Pi firewall is now operational and adhering to your specified rules. You can verify the status and view the active rules at any time with the command: sudo ufw status. And just like that, you've configured your very own Raspberry Pi firewall.
For those who are new to Raspberry Pi or Linux, there is much to learn. The initial steps of the process may seem daunting, but with a little bit of research and experimentation, the process will become much easier. Setting up a firewall is one of the most important steps to protect your Raspberry Pi.
To provide a more in depth look at the specifics of securing a Raspberry Pi, we have created a table with the information in more detail, and useful references
| Category | Details |
|---|---|
| Objective | Secure a Raspberry Pi from unauthorized access and cyber threats. |
| Importance | Protects sensitive data, prevents network breaches, and ensures device integrity. |
| Firewall Options | UFW (Uncomplicated Firewall), iptables. |
| UFW Installation | sudo apt install ufw |
| UFW Enablement | sudo ufw enable |
| UFW Status Check | sudo ufw status |
| Key Ports to Allow | Port 22 (SSH), Port 80 (HTTP), Port 443 (HTTPS), any others as needed. |
| Best Practice | Default deny all inbound, allow specific ports, disable password-based SSH. |
| Additional Security Measures | Update software, use strong passwords, consider disabling SSH password authentication, and enable automatic security updates. |
| Troubleshooting | Check firewall status, verify port access, and confirm network configuration if having issues. |
| Reference | Official Raspberry Pi Documentation |
- Stella Barey Age Biography Facts Unveiled
- Movierulz Latest Updates Alternatives Risks What You Need To Know